How to secure your server-side GTM measurement from DDoS attack
We'll be using additional server to intercept incoming requests that is addressed to our server-side gtm and configure basic rate-limiter to have control over incoming requests.
Hey there, random internet guy!
Today, i'd like to talk about how to secure your server-side google tag manager container from possible DDoS attacks. Before i start, i just want to mention that this topic will be highly related to tech stuff. So if you are not tech guy, just keep that in mind it's ok to understand NOTHING.
TL;DR
We'll be using additional server to intercept incoming requests that is addressed to our server-side gtm and configure basic rate-limiter to have control over incoming requests.
Well, i guess you already know what is it but i'll make short explanation anyway.
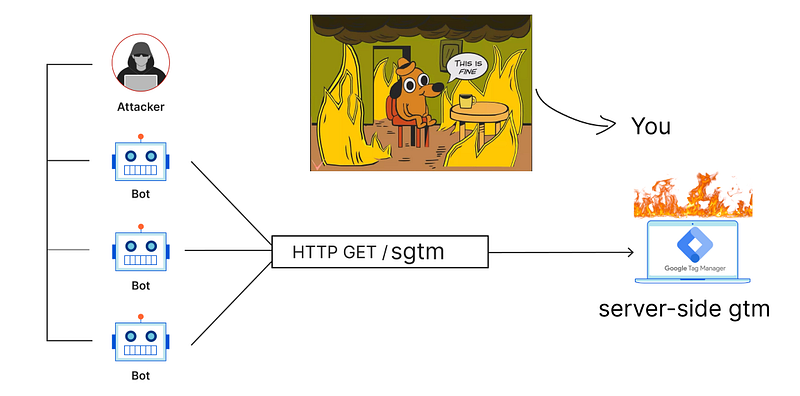
A DDoS (Distributed Denial of Service) attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic. It involves multiple systems (often compromised devices in a botnet) sending excessive requests simultaneously, making the target unavailable to legitimate users. This can result in downtime, performance degradation, or even a complete service shutdown.
When it comes to analytics tools, this kind of attack gains specific ability to create a harm: It can fuck up your ga4 data. If an attacker is smart enough (he/she probably is btw.) can manage the data that is being used in ddos attack and use it to manipulate the data collected by your analytics tools, such as Google Analytics 4 (GA4). By sending falsified or exaggerated data during the attack, the attacker can corrupt your analytics reports, making it difficult to distinguish legitimate traffic from malicious activity. This manipulation could lead to misleading insights, skewed metrics, and compromised decision-making based on inaccurate data.
For instance, the attacker might inflate pageviews, distort user behavior metrics, or create phantom conversions, rendering your analytics data unreliable. Recovering from such an attack often requires filtering out the fake data, which can be challenging, especially if the attack mimics realistic user behavior.
Before starting the solution part, i just want to mention that there is no SINGLE SOLUTION for this topic. I'll just cover the basics.
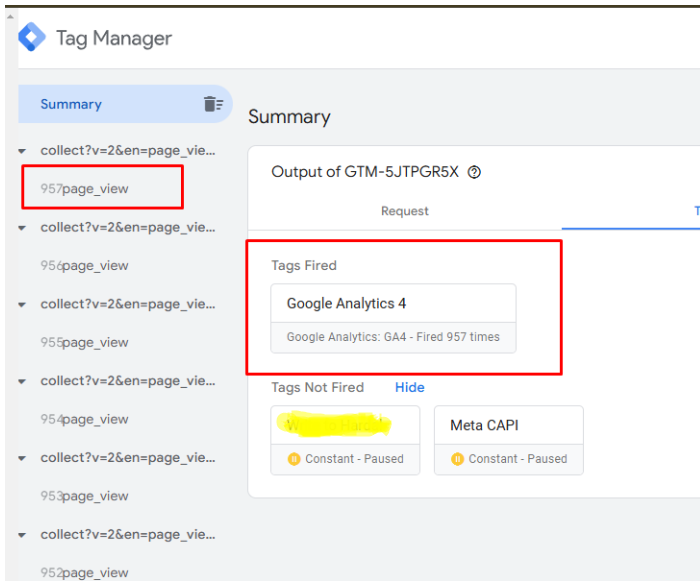
First, let's look how bad it looks like having a DDoS attack to server-side gtm container.
I'll be using native server-side gtm image for this test https://example.com/sgtm/healthy this is our target. I'll be using some stress test library for simulating a DDoS attack.
Now image this numbers way more bigger. Typical DDoS attacks comes from dozens of machines and hundreds if not thousands of requests per seconds. Good luck with cleaning all the mess from your marketing platforms.
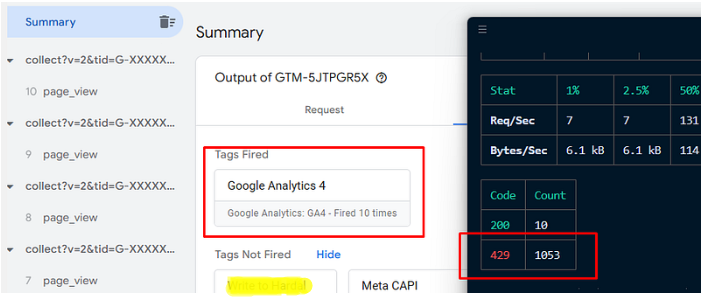
However, if you setup additional server to intercept the incoming request, you can use rate-limiter libraries to manage incoming requests. Since it can be too complex i just mention the summary:
Implemented additional server -> Send request to wrapper server instead of directly server-side gtm container -> setup rate limiter to allow only 10 request per minute for each IP -> redirect incoming requests to server-side gtm container from Local Network.
Before i go, i just want you to keep that in mind
There is no such thing as "unhackable"
Peace.